Why cobble together the right email solution?
Get everything you need for better, more successful email here at SocketLabs, from simple sending tools to deeply informative reporting. We have it all so you can, too.

Using our SMTP and API options, we help you deliver more mail without more complexity. Plus, we have affordable and flexible pricing options you can’t find anywhere else.
Turn those quick highlights into a deep understanding of what is impacting your scores and why, plus how to improve your performance with Guided Insights.

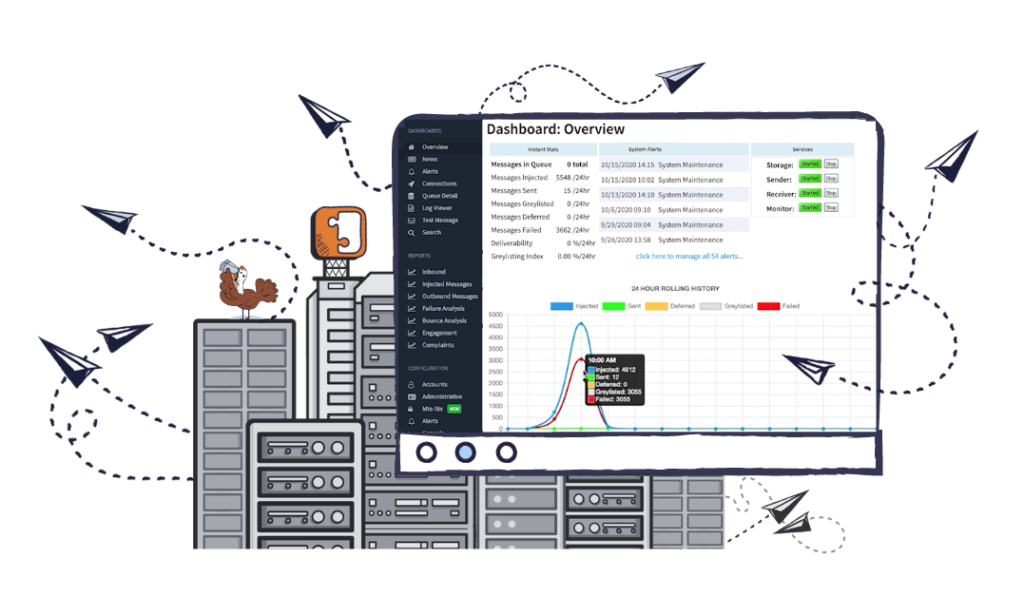
Hurricane can be licensed and configured to fit your needs and email volume, making it a highly customizable and dependable solution.
Unlike other ESPs, we really mean it. You’ve got the email. We’ve got infrastructure, data, tools, and the know-how. Let’s combine forces.



