- Why SocketLabs?
- By Function
- By Vertical
- By Use Case
- Why SocketLabs
Explore Spotlight
- Email Services
- Spotlight Email Analytics
- Resources
- Help
- Documentation
- Content
- Tools
Download our Newest Guide:
- Pricing
Security is where we take ourselves the most seriously, because we know it’s no laughing matter. Explore our Security Center to see what we mean.
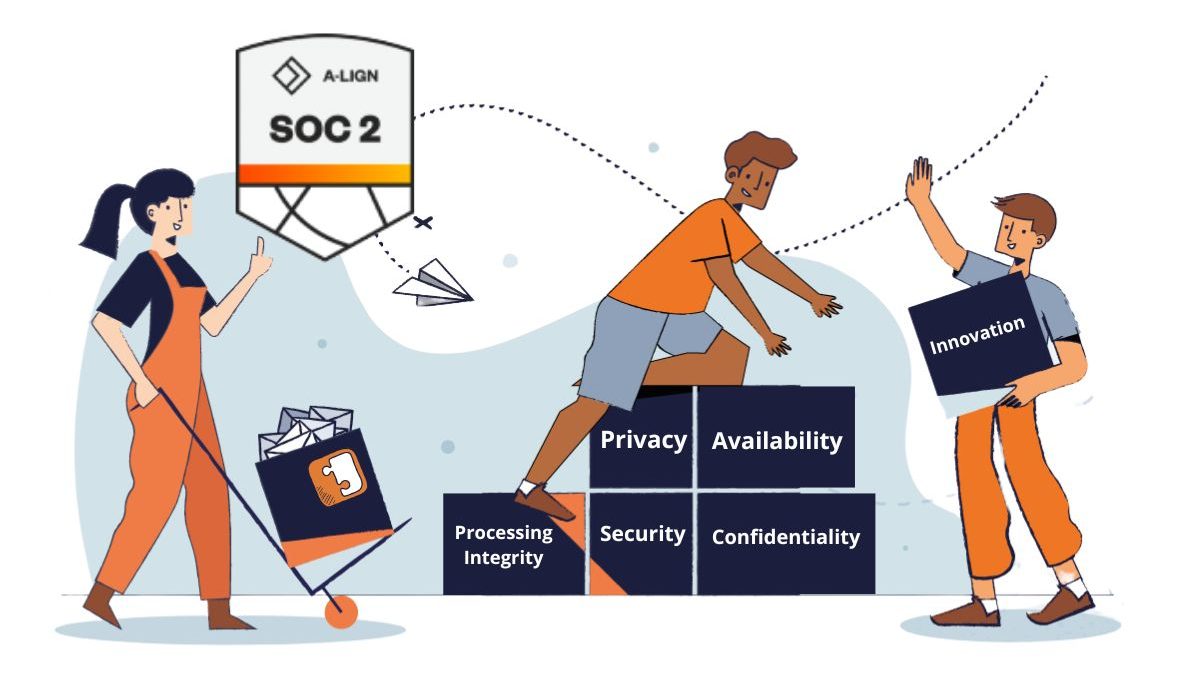
We work hard to maintain our SOC 2 Type 2 compliance. Each year, we undergo extensive and (exhaustive!) auditing to renew our commitment.


We’re proud members of the Messaging, Malware and Mobile Anti-Abuse Working Group (M3AAWG), where the industry comes together to work against bots, malware, spam, viruses, DoS attacks and other online exploitation.
Does the mail you send need to comply with all the rules and regulations of HIPAA? Our data practices are adherent with all the processing standards you need to stay compliant.
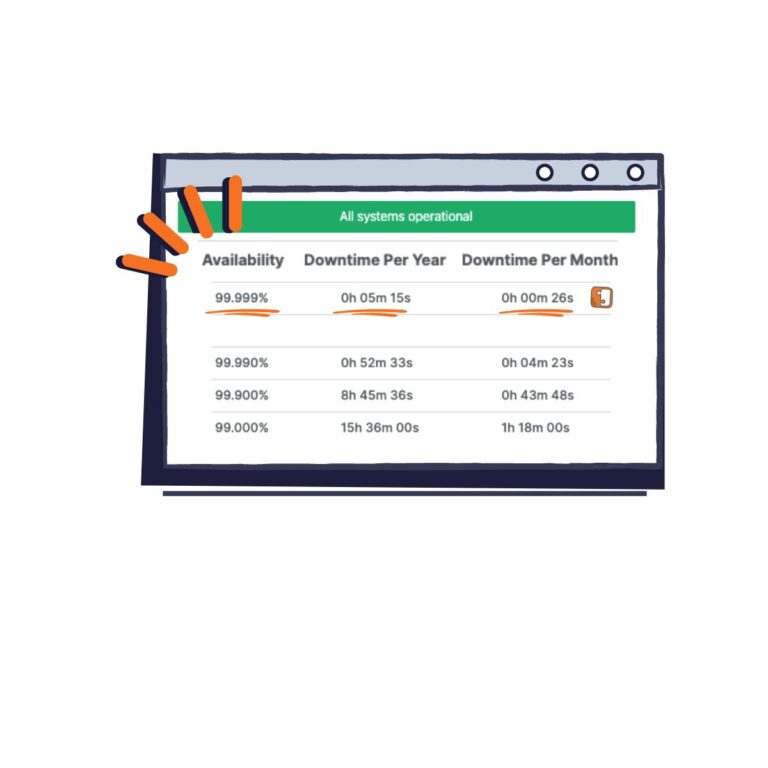
We are very happy to report we typically operate at 99.99% uptime, meaning you have a very low chance of any kind of outage creating delivery issues for you. You can put your faith in us.
Looking for our policies? Here’s a round-up of our data privacy, use, and processing policies.


© SocketLabs. All Rights Reserved.
