![]()
SocketLabs offers unique solution to allow simultaneous white-labeling and HTTPS link security for email
“The Chrome browser changes will significantly impact the sender’s perceived performance as their engagement statistics will show a significant decline.”
Over the last few months, Google has slowly been rolling out updates to the Chrome browser to improve security for its users. These changes, originally announced in late 2019 [https://blog.chromium.org/2019/10/no-more-mixed-messages-about-https.html] are focused on preventing the issue of mixed content. Mixed content refers to when a webpage is initially loaded over a secure HTTPS connection, while other page resources like images or stylesheets are loaded over a regular HTTP connection. The term “mixed content” comes from the fact that both HTTP and HTTPS content is being loaded to display the same page.
The exact rollout schedule originally provided by Google has changed several times, and there has been some confusion about what exactly is and isn’t going to be blocked in each release. [https://security.googleblog.com/2020/02/protecting-users-from-insecure_6.html]
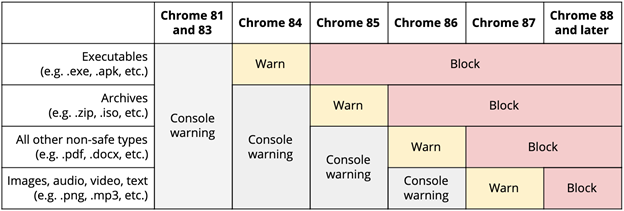
While we did not expect images to be impacted until Chrome 87, we’ve identified that Chrome 86 included a feature released that automatically changes HTTP image links to HTTPS [ https://www.chromestatus.com/features/4926989725073408 ]. Since the request doesn’t fallback to HTTP, this essentially blocks the request from occurring. With the upcoming release of Chrome 87, we expect that users will begin receiving a warning message when reading email messages without fully secured content, rather than the HTTPS upgrade errors simply being logged in the console.
How Does This Impact Email Senders?
This issue has a major impact on email senders in a number of different ways. The primary issue for most senders is referenced images like logos and other content images being served securely over HTTPS. For SocketLabs customers using the SocketLabs Email Template Designer and associated image management solution, all images are served over a CDN with proper HTTPS encryption. Our customers managing email content themselves and sending mail using our APIs and SMTP relay will need to be aware of how they are hosting images and ensure the images are hosted on a server properly configured to handle secure HTTPS requests.
The other major area in which these changes come into play is engagement tracking. Detection of an email “open” relies on the email client loading a zero-pixel image. With these changes to Chrome, tracking pixels hosted without proper HTTPS security may no longer work properly when the email is opened in a browser-based client.
Security and Branding with SocketLabs
Unlike message content images like logos or product shots, tracking pixels are much more likely to be managed by the ESP as tracking systems can be quite complex. This takes control of the use of HTTPS out of the hands of the sender. It forces ESPs supporting tracking to either use their own domain for the tracking pixels, to simplify the use of HTTPS security, or force customers through the nightmare of setting-up a reverse proxy configuration or managing certificates for all of their clients. Senders that use an ESP-owned domain for engagement tracking risk encountering URL reputation issues caused by other senders of that ESP. This is why here at SocketLabs we require all customers to white-label our engagement tracking domain.
The good news is our secure engagement tracking feature allows senders to achieve both proper white-labeling for reputation isolation and the HTTPS security required by Chrome to ensure all events are properly recorded. We do this by generating and managing. Let’s Encrypt SSL Certificates automatically for our customers. Combined with our management API, we allow clients to manage domains for engagement tracking with proper security at scale. This is a unique feature set not offered by any other Email API vendor.
How Big is the Problem?
These changes within Chrome have a major impact to the email community. This is due to the fact that, according to Litmus, about 40% of all email messages are viewed in web browsers [https://www.litmus.com/blog/infographic-the-2019-email-client-market-share/], and Chrome as a browser currently maintains an approximate 70% market share. Thus, it is likely that almost 30% of all email messages are viewed in the Chrome browser.
The good news is that the three largest US consumer webmail providers automatically proxy images displayed to users. These proxies utilize HTTPS to load the images between the proxy and the end-users securely. So, messages viewed in the Gmail, Verizon Media, and Microsoft (Hotmail/Outlook/Live) webmail clients will not be impacted.
Currently, Comcast is the largest mailbox provider that we can self-validate as impacted by the changes made by Chrome to prevent mixed content. We would expect most B2B webmail clients not operated by Google or Microsoft will also be impacted. In looking at customer data, we can see huge decreases in open rates at Comcast when Secure Engagement Tracking is not applied. For example, one client experienced a 78% month-over-month open rate decrease at Comcast and a 25% decrease in opens to non-consumer addresses.
It is likely that senders across any ESP without proper support for secure engagement tracking are going to be experiencing declines in perceived open rates. With Q4 being a time of year when sender volumes rise, possible perceived declines in performance is going to be a scary thing for many marketers and senders.
For more information read the blog SocketLabs Introduces Encrypted Engagement Tracking.